
Large community and religious WhatsApp groups are being targeted by scammers who infiltrate them to try and deceive their members into sending them money. Since January of this year, 268 people have reported falling victim to this scam.
The fraud often begins when a member of the group receives a WhatsApp audio call from the fraudster, pretending, or claiming, to be a member of the group. This is done in order to gain the individual’s trust, and often the scammer will use a false profile picture and / or display name, so at first glance it would appear to be a genuine member of the group.
The fraudster will then call the victim and say they are sending a one-time passcode which will allow them to join an upcoming video call for group members. The scammer then asks the victim to share this passcode with them so they can be “registered” for the video call. What’s really happening is that the scammer is asking for a registration code to register the victim’s WhatsApp account to a new device where they then “port” their WhatsApp profile over.
Using a quick start package may be the quickest way to get a fully set up , add your content site. but are you aware of the dangers.
we tested several quick starts from major providers ranging from Template developers and extension developers who include a ready to go version of Joomla.
We found that there were varying degrees of insecurities. None of these packages are plug/play/forget.
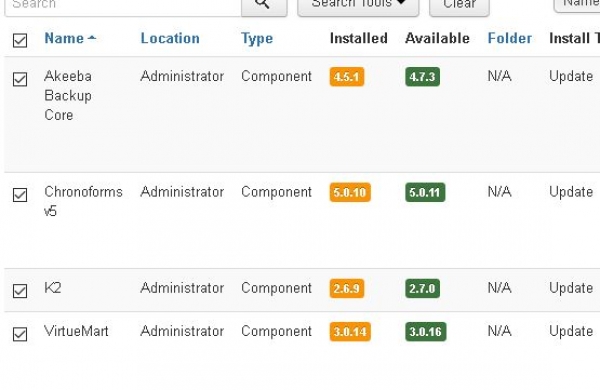
The most common issue and vulnerability was the use of out of date version of Joomla. When (at the time of writing) Joomla is 3.5.1 we found the worst case was 3.3.1 with several security vulnerabilities. Possibly the worst one was an extension developer charging for a download that included 2.5.29
Using a quick start package may be the quickest way to get a fully set up , add your content site. but are you aware of the dangers.
we tested several quick starts from major providers ranging from Template developers and extension developers who include a ready to go version of Joomla.
We found that there were varying degrees of insecurities. None of these packages are plug/play/forget.
The most common issue and vulnerability was the use of out of date version of Joomla. When (at the time of writing) Joomla is 3.5.1 we found the worst case was 3.3.1 with several security vulnerabilities. Possibly the worst one was an extension developer charging for a download that included 2.5.29

While checking my site logs, as should be standard practice for everyone, I discovered an unintentional honeytrap.
Q. What is the point of trying to hack an rss feed and is it possible?
In Joomla we are using usernames and passwords. It is crucial that you create a strong username and strong password to protect your Joomla website when creating a user account in your site.
Any Joomla web site that employs usernames and passwords must be administered with dedicated attention to ensuring that good security practices are followed by all users. If you as site administrator or your users are careless about how they choose usernames and passwords or store credentials, then a "hacker" or a "botnet"" may find it relatively easy to break your site's security.
Read more: The Importance of Using a Strong Username & Password